The unattended upgrades feature on Debian-based distros is very handy way to ensure that you are running up-to-date security patches and latest versions of software running. At some point when you reach a certain limit of running instances, like VMs and containers, it starts to be hard and time consuming to keep them all updated. I have servers running locally in my homelab, as well as numerous instances in the cloud.
Previously I used to mark 1 day in a week when I would go through all the instances and update them manually, but eventually it became a very time consuming task, so I ended up pushing the date to start it.
Unattendend upgrades works very well in my setup, and below I will explain how to enable it on Ubuntu, Debian or any other Debian-based distro.
First steps and installing packages
First, install the required package sudo apt-get install unattended-upgrades -y
Run sudo dpkg-reconfigure -plow unattended-upgrades
It will prompt you asking whether you want to download and install stable updates.
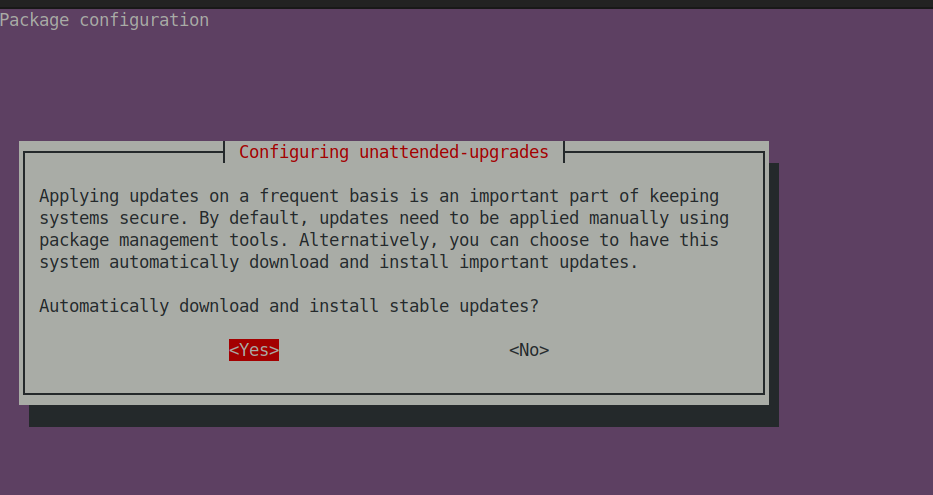
Select Yes and press enter.
Configure unattended upgrades
sudoedit /etc/apt/apt.conf.d/50unattended-upgrades to open a config file
Uncomment (remove //) from the Security line. This will install the security updates by default.
Alternatively you can also uncomment the updates line to install all updates.
The config will look something like:
Unattended-Upgrade::Origins-Pattern {
// Codename based matching:
// This will follow the migration of a release through different
// archives (e.g. from testing to stable and later oldstable).
// Software will be the latest available for the named release,
// but the Debian release itself will not be automatically upgraded.
// "origin=Debian,codename=${distro_codename}-updates";
// "origin=Debian,codename=${distro_codename}-proposed-updates";
"origin=Debian,codename=${distro_codename},label=Debian";
"origin=Debian,codename=${distro_codename},label=Debian-Security";
Next, you want to uncomment the setting and set the value to true Unattended-Upgrade::Automatic-Reboot "true" to enable automatic reboot.
You can also configure other settings, such as e-mail reports, reboot time among others. Personally I like to set the reboot time at 02:00 AM. Make sure to save the config file after you edit.
Optional: Deleting dependecies
It’s a good idea, though not mandatory to auto delete dependencies as well:
// Remove unused automatically installed kernel-related packages
// (kernel images, kernel headers and kernel version locked tools).
Unattended-Upgrade::Remove-Unused-Kernel-Packages "true";
// Do automatic removal of newly unused dependencies after the upgrade
Unattended-Upgrade::Remove-New-Unused-Dependencies "true";
// Do automatic removal of unused packages after the upgrade
// (equivalent to apt-get autoremove)
Unattended-Upgrade::Remove-Unused-Dependencies "true";
Test unattended upgrades
You can verify that the upgrades are working by running
sudo unattended-upgrades --dry-run --debug
Checking update logs
You can check the log files with sudo cat /var/log/unattended-upgrades/unattended-upgrades.log
Checking upgrade schedules and timers
systemctl | grep -w 'apt'will show you periodic apt maintenance tasks:
apt-daily-upgrade.timer loaded active waiting Daily apt upgrade and clean activities
apt-daily.timer loaded active waiting Daily apt download activities
- You can view the download schedules using
systemctlcommand:
systemctl cat apt-daily.timer
systemctl cat apt-daily-upgrade.timer
Final words
Unattended updates for Debian -based Linux systems help to keep your severs up-to-date. It is very simple and easy way to protect against threats and vulnerabilities. Especially if you running multiple servers, this method is very efficient and time saving.
More info can be found on Debian Wiki page.
Revisons
2024-05-02: Updated some confifguration steps on removing dependecies and choosing which files to update.